What Is SSH?
SSH or Secure Shell allows people to have remote access to their servers. It uses cryptographic techniques to make sure all communication to and from the server happens in an encrypted way.
It gives you a method of authenticating remote users, transferring inputs from the client to the host and relay information back to the client.
Linux and macOS users can use the terminal to SSH into their remote server directly. Windows users have to use something like Putty.
You're able to use shell commands in the same way you would if you were physically using the remote computer.
Starting an SSH session.
The SSH command has three pieces;
ssh {user}@{host}
- SSH tells the system that you want to open an encrypted connection.
- User is for the account you want to access (root === admin for example).
- Host is the computer you want to access (an IP address or domain).
After entering these you'll be asked for the password, although nothing shows on the screen, your password is being sent over.
SSH Encryption Techniques.
- Symmetrical encryption
- Asymmetrical encryption
- Hashing
Symmetric Encryption
This type of encryption (I hate typing this word) uses a secret key, used for both encryption and decryption of a message on both sides.
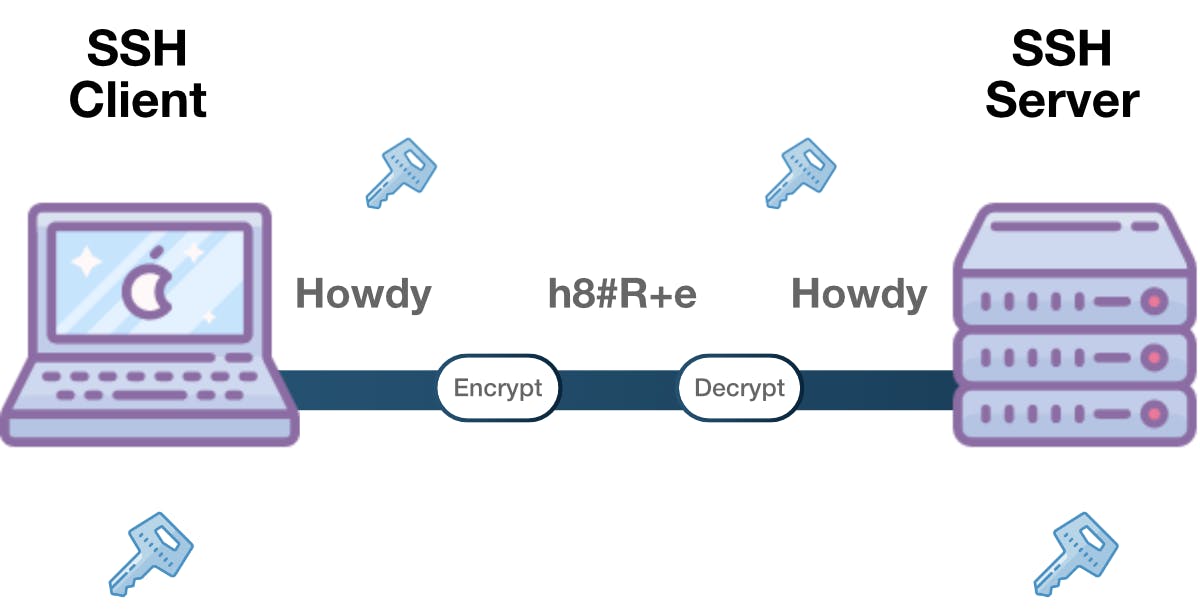
Typically called a shared key or shared secret encryption.
Usually there is one key but you can also have pair keys where one can calculate the other.
Both the client and the server get the key by using an agreed method (key exchange algorithm) and this key is never shown to any third party.
The information shared between server and client can be intercepted by another machine but it won't be able to calculate the key exchange algorithm.
There are many ciphers that exist to create keys, but one is chosen by order of preference of the two machiens prior to making secure transfers.
Asymmetric Encryption
Here we use two different keys for encryption and decryption.
- Public Key
- Private Key
- Public-Private key pair
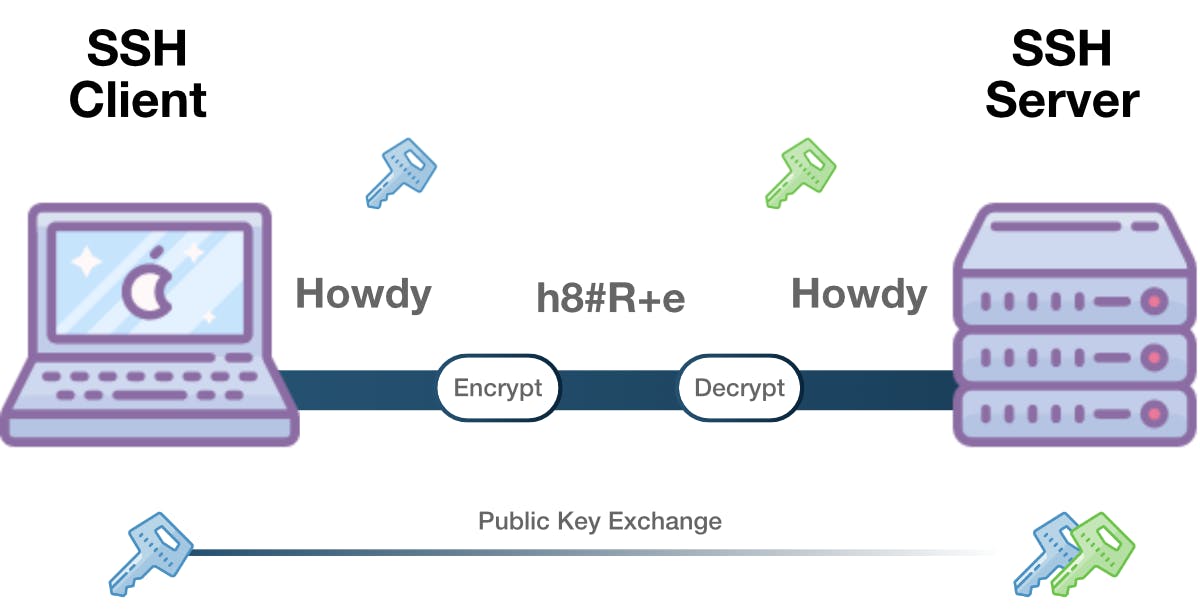
This is like a one way relationship. Public is public but you're not able to figure out private key based on the public one. The relationship between the two is complex.
This one way relationship means that a public key can not decrypt it's OWN messages nor anything sent by the private key.
It's not used to encrypt the entire session, but only during the key exchange algorithm.
Before a secure connection both machines create temporary public-private key paids and share them to create a shared secret key.
Once a secured symmetric communication has been made, the server uses the client's public key to challenge and send it to the client for authentication.
If the client can decrypt the message, it means that it has the private key. Then the SSH session can get started.
Hashing
One way communication that is never meant to be decrypted. Hashing generates a unique value of a fixed length for every character in the communication being transferred.
This makes it almost impossible to reverse engineering (until quantum computing comes ;) ).
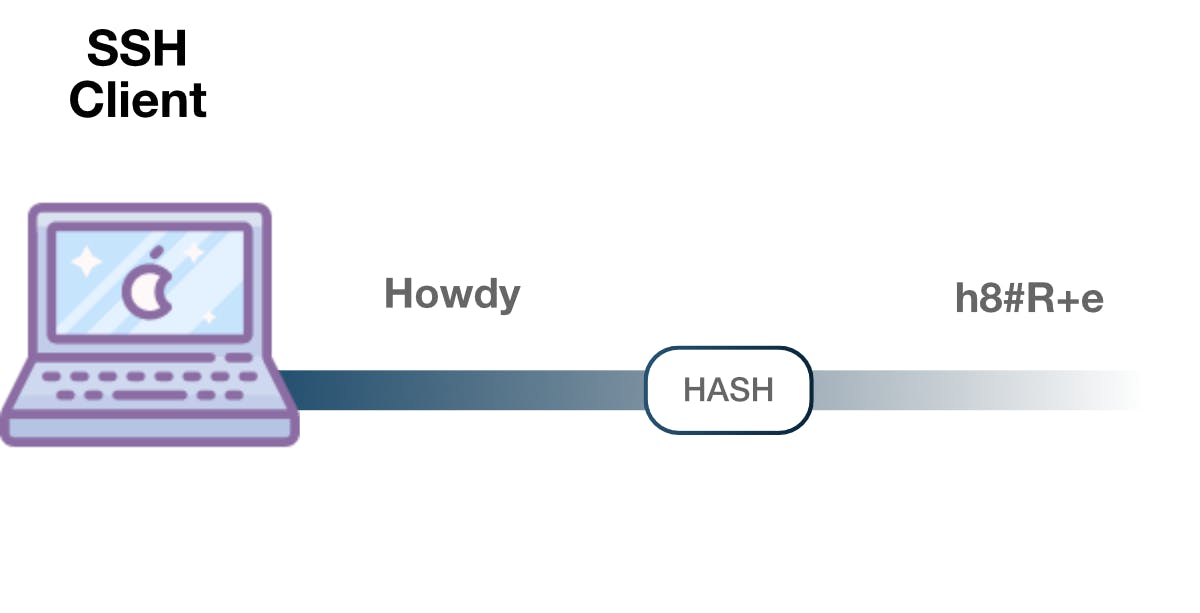
It's easy to generate a hash from an input so if the client has the correct input, they can compare it to the hash and confirm that they have the correct input.
SSH uses hashes to verify the validity of a message.
HMAC -> Hash-based Message Authentication Codes are used the make sure the infomation has not been intercepted or changed.
While choosing a symmetrical encryption algorithim, a message authentication algorithim is also craeted, like the selection of ciphers above.
MAC
Each message must contain a MAC. This is calculated using the symmetric key, packet sequence number and message contents.
The MAC is sent outside of the symmetric key and is the final piece of the communication during the session.
How Does SSH Work with These Types Of Encryption?
SSH works on TCP port 22 by default (not a fixed port). The server listens on port 22 for incomming connections.
An secure connection is authenticated and and then a shell enviroment is started.
The client machine has to begin the connection by starting a TCP handshake with the server, confirming a secured symmteric connection.
It has to verify that the server ID matches prvious records which are usually kept in an RDA key store file.
The connection has two stages, first both machines must agree on the encryption standards and then the user has to be authenticated with their password etc.

